privileges benevolences Positive aspects courtesies mercies indulgences graces favors pros waivers boons dispensations licences blessings turns licenses liberties mannas godsends
"It is truly regrettable that we are going to be pressured to allocate significant the perfect time to issues unrelated to recreation improvement due to this lawsuit," — Palworld responds to information of Nintendo suing for patent infringement
Some administrators counsel that you just alter the default port that SSH runs on. This may aid lessen the quantity of authentication tries your server is subjected to from automatic bots.
The SSH daemon could be configured to instantly ahead the Show of X purposes to the server towards the shopper device. For this to function accurately, the consumer needs to have an X windows system configured and enabled.
Obtain legal assets and assistance to be familiar with your enterprise obligations and comply with the regulation.
When you are working with an internet transfer protocol, you might want to obtain the firewall access. Usually, the firewall could block and interrupt your relationship.
SSH connections may be used to tunnel site visitors from ports about the neighborhood host to ports on a distant host.
Just about the most beneficial function of OpenSSH that goes mainly unnoticed is a chance to Manage certain components of the session from in the connection.
It's also possible to check out other techniques to help and servicessh configure the SSH service on Linux. This method will inquire the user to create a directory to configure and retailer the information.
A distant Git repository which you want to obtain. We'll use a GitLab repository for this article; on the other hand, the method are going to be very similar for other Git management vendors.
To empower this performance, log in for your distant server and edit the sshd_config file as root or with sudo privileges:
For that reason, you should place your most standard matches at the highest. For illustration, you could default all connections to not permit X forwarding, with the override for your_domain by possessing this in your file:
When you total the steps, the service will enable and start immediately on reboot according to the command you made use of.
Password logins are encrypted and so are straightforward to understand For brand spanking new consumers. However, automatic bots and malicious end users will frequently regularly make an effort to authenticate to accounts that allow for password-based mostly logins, which can lead to safety compromises.
 Marla Sokoloff Then & Now!
Marla Sokoloff Then & Now!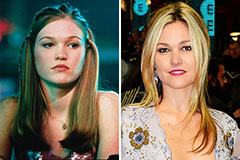 Julia Stiles Then & Now!
Julia Stiles Then & Now! Elisabeth Shue Then & Now!
Elisabeth Shue Then & Now! Dolly Parton Then & Now!
Dolly Parton Then & Now! Richard Dean Anderson Then & Now!
Richard Dean Anderson Then & Now!